ICT Security
The paradoxical situation of contemporary ICT: openness vs. security
The need for closer alignment of information systems with the company's business strategy today points to security as a key issue. Given that contemporary corporate ICT requires an ever greater degree of connection of the company to the outside world (smartphones, netbooks, B2B, B2C portals), the exchange of information within the organization and its immediate environment has never been as critical as it is today. Many previously neglected risks are suddenly real.
Security incident as part of real life
The media and real life constantly remind us that no one is immune to a possible security incident:
- virus infection
- hacker attack
- identity abuse (password, key)
- loss, theft or misuse of confidential data
- data corruption
- …
The consequences of these incidents can be very serious for any organization that becomes a victim of a security breach and always include significant direct or indirect financial losses.
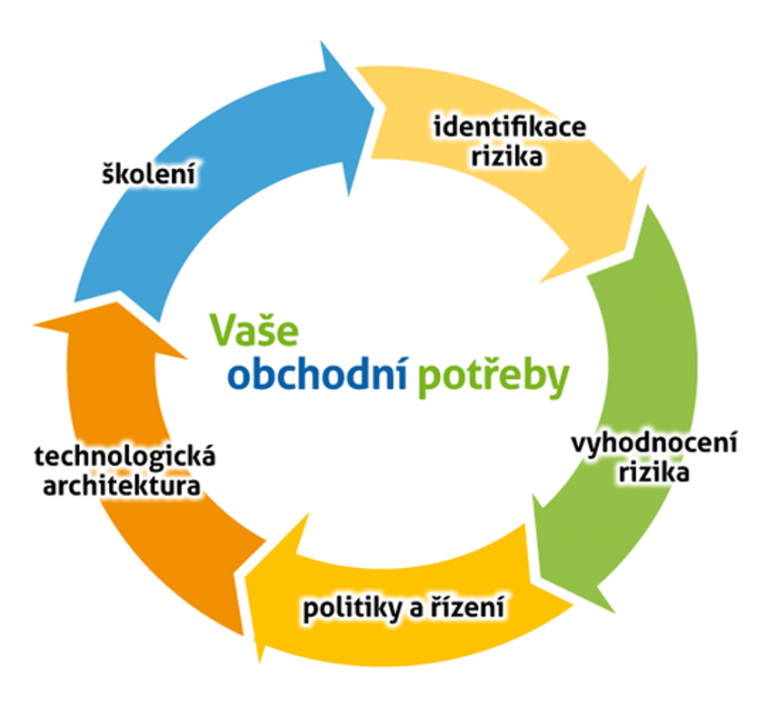
Security: Protection or Containment
It would be easy and simplistic to see security only as an impenetrable fortress and a permanent defense against attacks and threats. This relatively narrow view of the issue of security often results in an emphasis on technology-oriented solutions.
Today, however, we need a completely new approach. One that is focused on creating added value and focuses on people and business processes. We need security that is not only defensive in nature, but is able to respond to changing conditions in the open world. Security should not become a prison for users.
What I do not manage, I do not control, or integration as a necessity
Many companies live in the belief that they have already implemented all the important technological measures in terms of security. The purpose of the first implementations of network antivirus solutions, firewalls, IDS and IPS, was primarily to protect the perimeter of the ICT infrastructure itself.
Then came the means whose task was to eliminate the risks of internal misuse of ICT resources: multi-factor authentication systems, network access control (NAC) and, more recently, data leakage prevention (DLP) systems.
However, we are currently facing much more sophisticated attacks both from the outside and from the inside, and therefore it is necessary to integrate and manage the entire, historically insular-oriented security. We are forced to collect, evaluate, report and archive security incidents centrally with an immediate response to the most serious ones.
Our company's approach to the topic of ICT security is based on the belief that a quality security solution is able to create added value. However, this is only possible if it is oriented towards the customer's business goals, is in line with the company's strategy and is of course able to adapt to changing conditions.
The appropriate integration of existing security solutions and their addition with others so that ICT security can be realistically managed is one of the key parameters of the quality of our services.
Why choose Service & Support:
- Any successful implementation of an individual security solution is certainly a good project - but we want our customers to realistically manage the security of their ICT.
- We understand your business as unique and therefore the implemented solution must perfectly suit it
- We see the implemented solution throughout the entire life cycle from the initial audit to operational support
- We try to focus on the real return on the implemented solution
- Our experts have experience from both TOP 50 companies and medium-sized dynamic companies
- We use proven methodologies: ISO 2700x, ITIL and other standards-based procedures
- Our technology partners are among the leaders in their field